Mastering Policy Flexibility: Understanding Configuration Scope in Strata Cloud Manager (SCM)

In today's dynamic security landscape, managing security policies across diverse environments – from physical firewalls in data centers to cloud-based instances and remote access users – demands a platform that offers both broad control and granular flexibility. Palo Alto Networks' Strata Cloud Manager (SCM) addresses this challenge with its innovative configuration scope feature. Moving beyond the traditional device group and template concepts found in Panorama, SCM introduces a new approach centred around folders and snippets to enable flexible policy enforcement.
🔧 Configuration Scope: Your View of Policy Applicability
At its heart, SCM's configuration scope determines where settings and policies can be applied. It allows you to enforce policies globally across your entire security platform, or target settings to specific parts of your organisation. The user interface in SCM keeps the current Configuration Scope always visible, and you can easily toggle your view to manage settings that apply more broadly or more granularly.
This visibility is crucial for understanding which configuration elements are applicable to the scope you're currently working in. To further aid administrators, SCM uses color-coded configuration indicators:
⚪ A Grey dot indicates configuration that is inherited from a higher level in the hierarchy.
🟣 A Purple dot signifies a predefined configuration, potentially from SCM defaults or Palo Alto Networks provided snippets.
🔵 A Blue dot means the object is present in the current configuration scope, either defined locally or applicable directly to the view you are in. These indicators help you quickly understand the source and applicability of configurations, making it easier to manage complex policy sets.
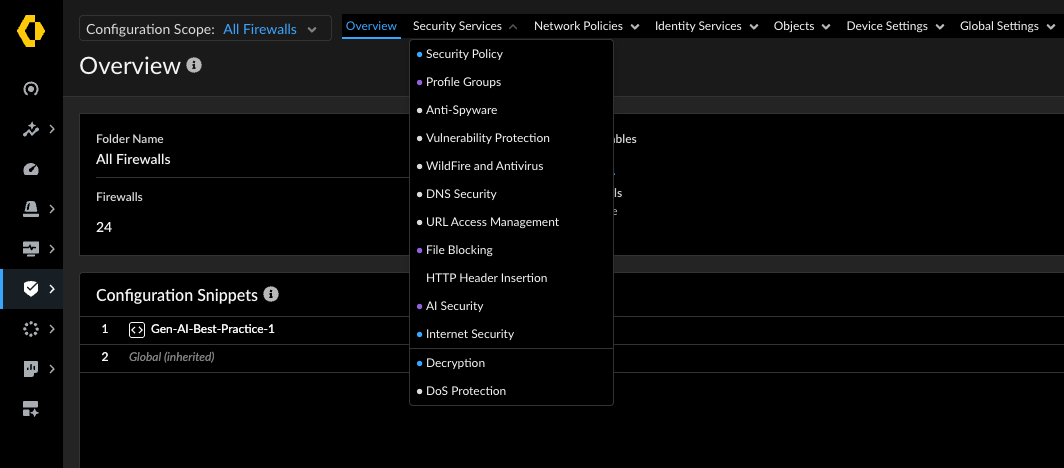
📁 Folders: Building Your Configuration Hierarchy
Folders are the primary configuration containers in SCM. They hold all aspects of your firewall configuration, including security rules, objects, networks, and device settings. SCM allows you to create a hierarchical structure of folders, typically under the predefined "All Firewalls" folder.
The key benefit of this folder hierarchy is configuration inheritance. Settings defined in a higher-level folder are automatically inherited by sub-folders and the firewalls placed within those folders. This is ideal for applying common policies that should apply to many devices, such as standard security profiles or network objects. While you can override inherited configurations in lower-level folders to customise for specific needs, you cannot delete inherited configurations at the lower level. This structure encourages placing common configurations higher up to avoid repetition. The folder hierarchy has a limit of four nested levels below the "All Firewalls" folder.
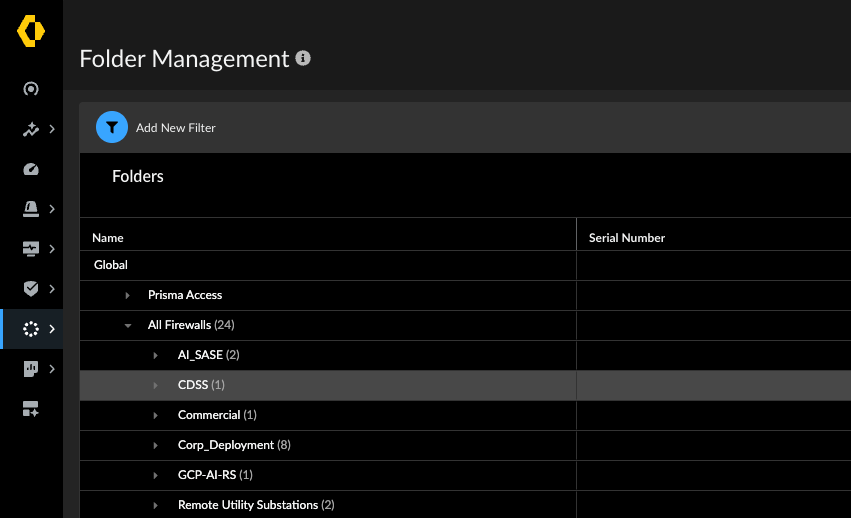
📂 SCM includes several important predefined folders:
•Global: The parent folder for everything, including Prisma Access and All Firewalls. Policies here apply to your entire security platform.
•Prisma Access Containers: Specific folders for Prisma Access components like Mobile Users and Remote Networks (these are predefined and users cannot add subfolders here).
•All Firewalls: A subfolder of Global and the parent folder for all your hardware and VM-Series NGFWs onboarded to SCM.
•Firewall Device: Each individual firewall onboarded acts as its own folder, allowing for per-device level configuration.
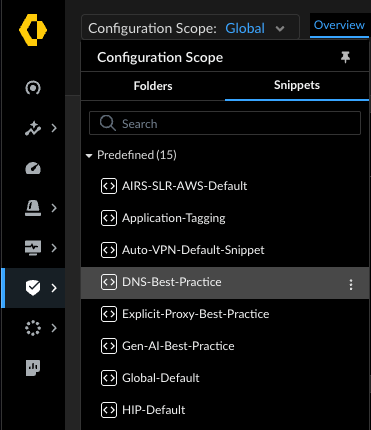
✂️ Snippets: Modularity and Targeted Application
Complementing folders are snippets, another type of configuration container. Snippets can also hold any part of your firewall configuration. However, unlike folders, snippets are not applied by default when created. They act more like templates for configuration.
The primary function of snippets is to provide modularity and enable targeted application of configurations. You explicitly associate a snippet with a specific folder or device. This is particularly useful for configurations that are needed only by a subset of firewalls within a folder, where placing the configuration in the parent folder would cause unwanted inheritance.
Snippets allow you to break down complex configurations into smaller, reusable blocks. Changes made to a snippet automatically update all associated folders and devices. Furthermore, snippets can be shared across different SCM tenants, even if they aren't linked to the same Customer Support Portal (CSP). Palo Alto Networks also provides predefined snippets with best practice configurations, like securing Office 365.
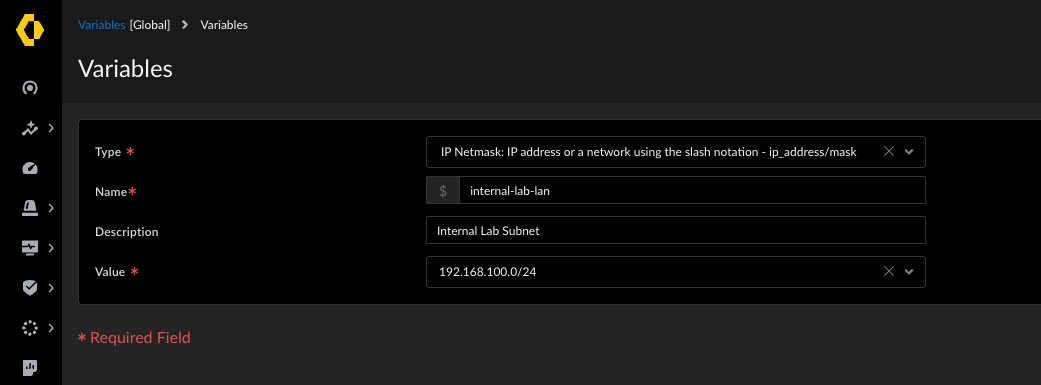
⚙️ Variables: Handling Device-Specific Differences
To manage variations like IP addresses or interface assignments within shared configurations, SCM utilises variables. Similar to Panorama, you can define a variable name and assign values. The scope of variables in SCM has been extended to include interfaces and zones. You can define variables at higher folder levels and override their values in sub-folders or associated snippets to accommodate device- or deployment-specific settings without replicating large configuration blocks.
✅ Putting it Together for Flexible Policy Enforcement
SCM's configuration scope, powered by the combination of hierarchical folders, flexible snippet associations, and variable overrides, creates a robust system for flexible policy enforcement. You can establish broad, common policies using folder inheritance, apply reusable configuration blocks where needed using snippets, and handle device-specific details using variables. The configuration scope indicators and toggleable view help administrators navigate and understand how policies apply across their environment.
While SCM is still evolving (feature parity with Panorama is not yet 100%), its cloud-native design and the flexibility offered by the configuration scope model position it as the direction for future firewall management, especially for greenfield deployments. For existing Panorama users, visibility can be gained by forwarding logs and telemetry to SCM's Strata Logging Service (formerly CDL/Data Lake), while configuration migration currently requires Professional Services.
By leveraging the configuration scope, folders, and snippets in SCM, organisations can streamline their security policy management, ensuring consistent enforcement while maintaining the agility to adapt configurations to specific needs.