Panorama Templates and Template Stacks

Templates and Template Stacks are used to configure firewalls using Panorama so that they can function on the network. If we look at the Panorama tabs, you can see that Templates encompass both the Network and Device tabs. The network tab is where we can define interfaces, Zones, Virtual Routers and so on, and the device tab is where we can configure server profiles like SNMP traps, Syslog, RADIUS authentication etcetera.These are exactly the same tabs you would see when logged directly into firewalls Web-Ui.
Panorama supports up to 1,024 Template stacks and each stack can have a maximum of 8 templates assigned.
Let's review the firewalls in the managed device summary, in my lab, I currently have two pairs of Active/Passive firewalls, FW01/02 is one pair and FW03/04 is another pair
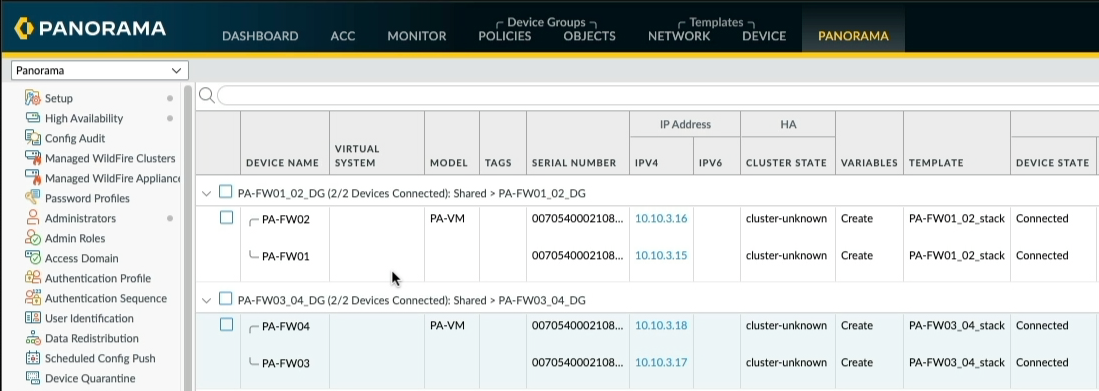
You see in the Template column that each pair of firewalls are associated with a unique Template Stack. A Template Stack is essentially a bucket that contains multiple templates, 8 being the maximum that can be applied to multiple firewalls.
These Templates and Template stacks were created when I imported the High-Availability firewalls into Panorama, if you haven't seen my "How to migrate a High Availability pair of PAN-OS firewalls into Panorama video yet I recommend you watch it so you can understand how & why the templates and templates stacks were created.
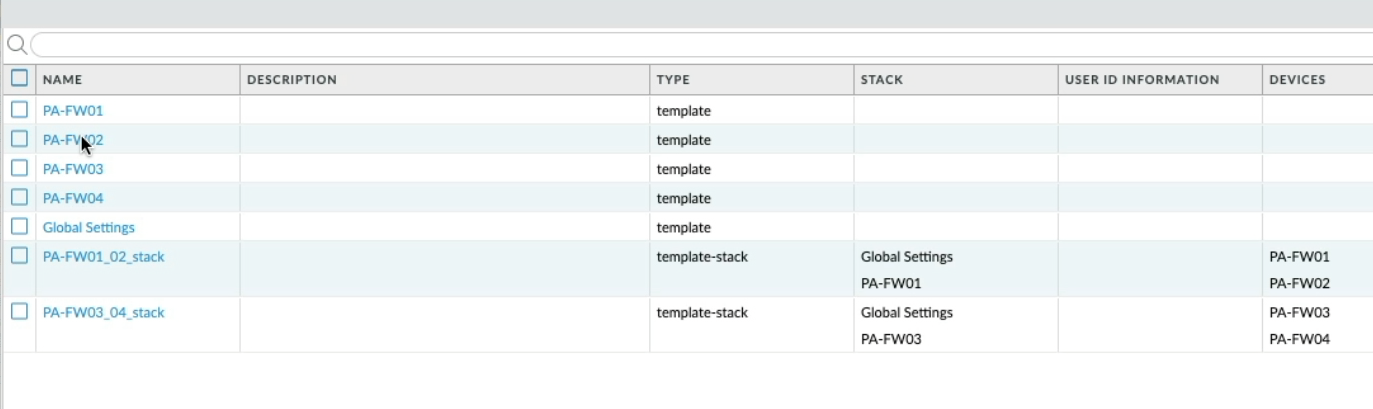
Let's take a look at the Templates, we can see there is a unique template for each managed firewall, however, because these are active/Passive HA pairs we are only interested in PA-FW01 and PA-FW03 templates as these are where the network configuration has been applied and added to the respective Template stacks.
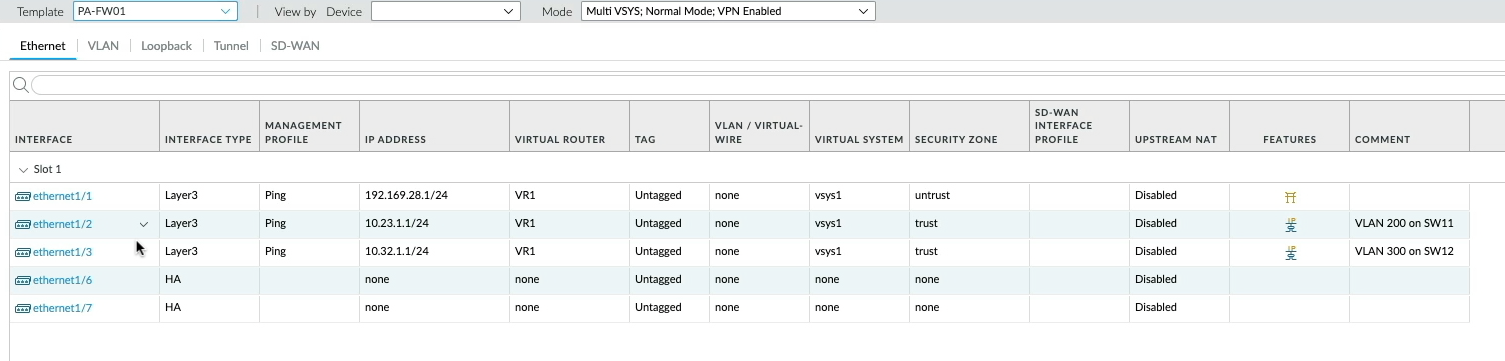
For example, if we clicked on the Networks tab, making sure we have the PA-FW01 template selected, we can see all the interfaces, IP addresses etcetera that has been configured and pushed to FW01 and in turn, FW01 synchronises to FW02 excluding the IP addresses as the passive device will only inherit the IP addresses when a failover event occurs.
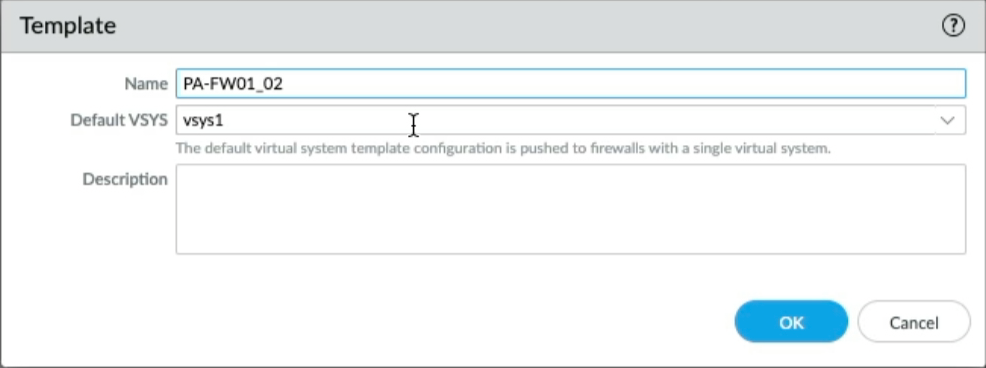
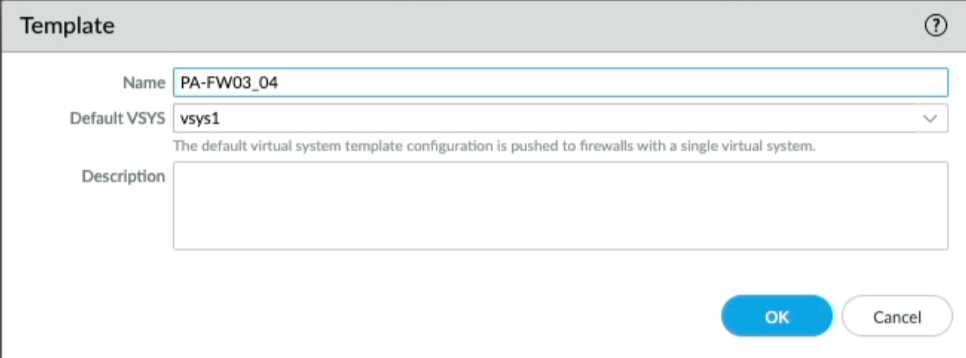
You will notice that PA-FW01 and PA-FW03 are the only templates referenced in the respective Template Stacks. To clean up the template configuration and make things simpler I could rename each of the active firewalls templates, so If I click on the PA-FW01 template and rename it to PA-FW01_02 you will see the template name changes within the Template stack, let's do the same for PA-FW03, name it PA-FW03_04.
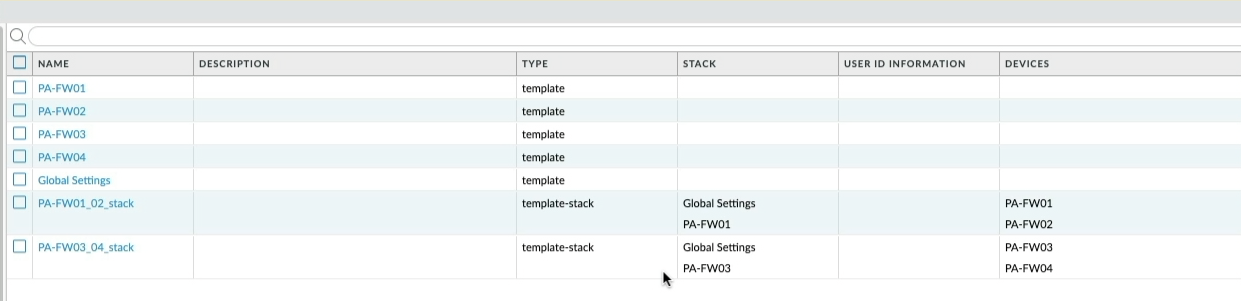
Both PA-FW02 and PA-FW04 are now obsolete so I can delete them from Panorama, commit that change to Panorama and push it to the firewalls.
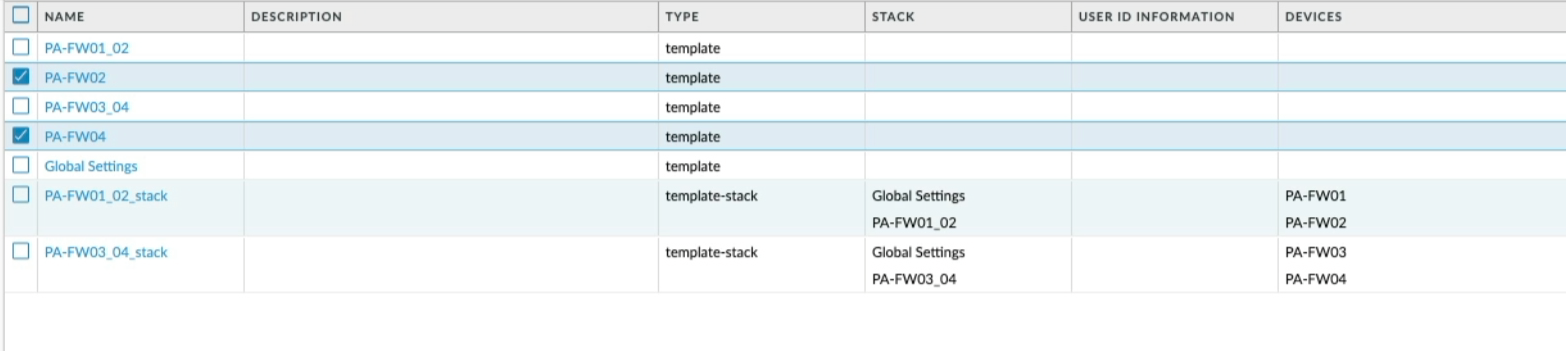
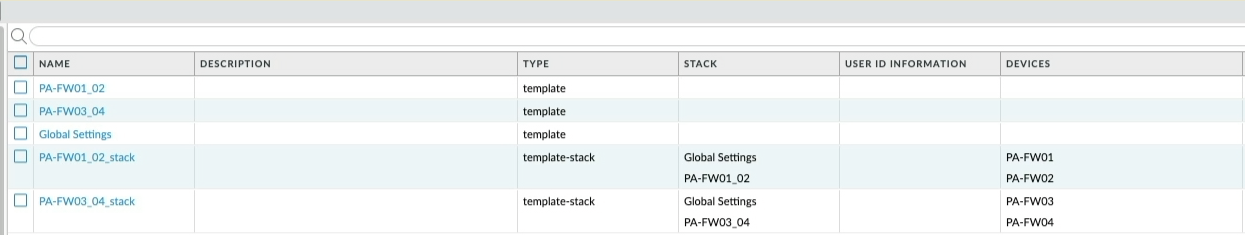
Let me demonstrate a simple template change, let's say I wanted to add an additional interface to both PA-FW01/02, first I would make sure the PA-FW01_02 template is selected, add interface Eth1/8 and commit the template changes and push to the firewall.
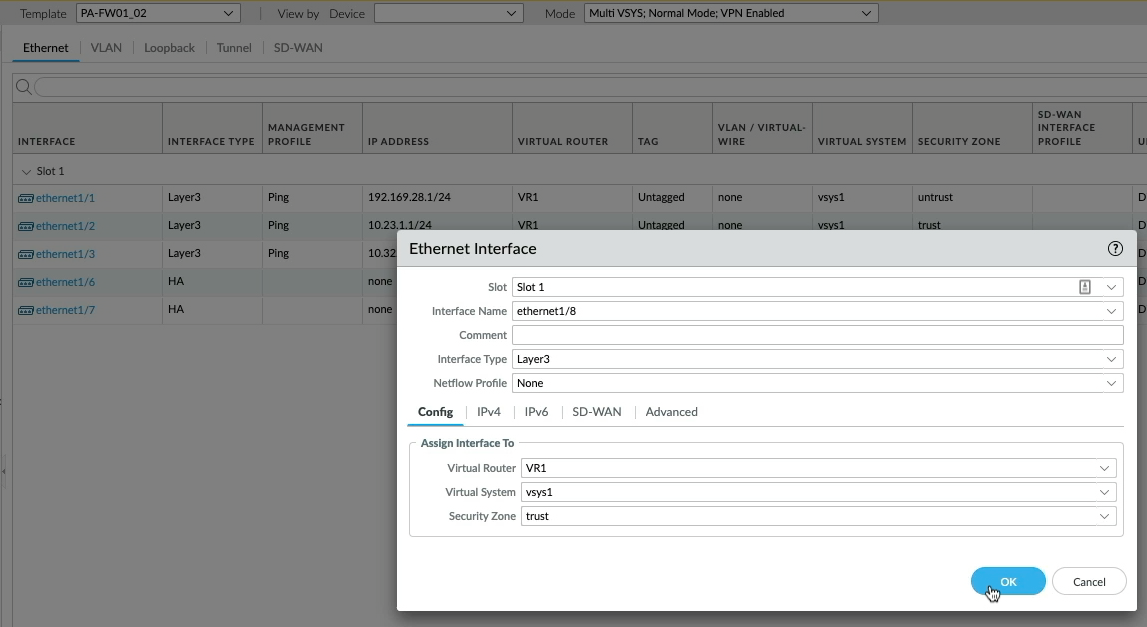
If I click on tasks down here and observe the "
"Commit all" task, you can see the commit was applied to the PA-FW01_02 stack.
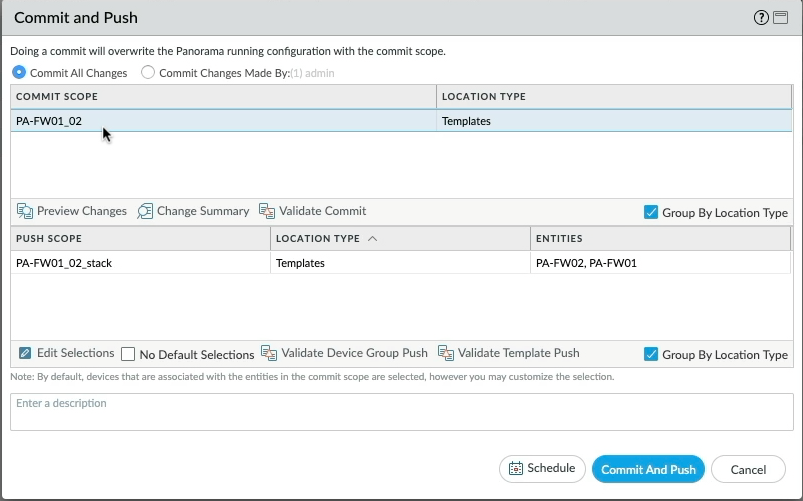
To confirm the template interface change was successful, we can context switch from Panorama or browse directly to the PA-FW01 management interface and then to the network tab and select interfaces. We can see that Ethernet1/8 has been added, this configuration would have also been sent to FW02 as well. Pretty straight forward right?
So that example took care of one pair of firewalls, but what about making changes to multiple firewalls, this is where templates and template stacks become very useful and save lots of time when making common changes and applying them to multiple firewalls in the firewall estate.
Let's go back to Panorama, and back to Templates, you can see I've created a Global settings Template and it has been added to each of the template stacks here.
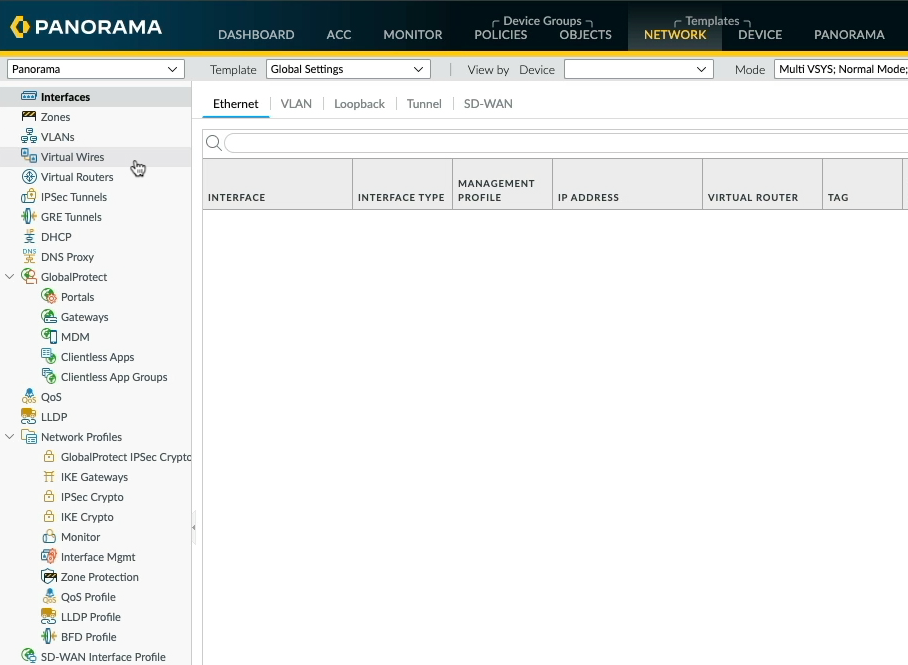
If I click on the network tab again and select "Global Settings" from the drop-down, I can tell straight away that the "Global Settings" template doesn't have any network settings, how do I know that?
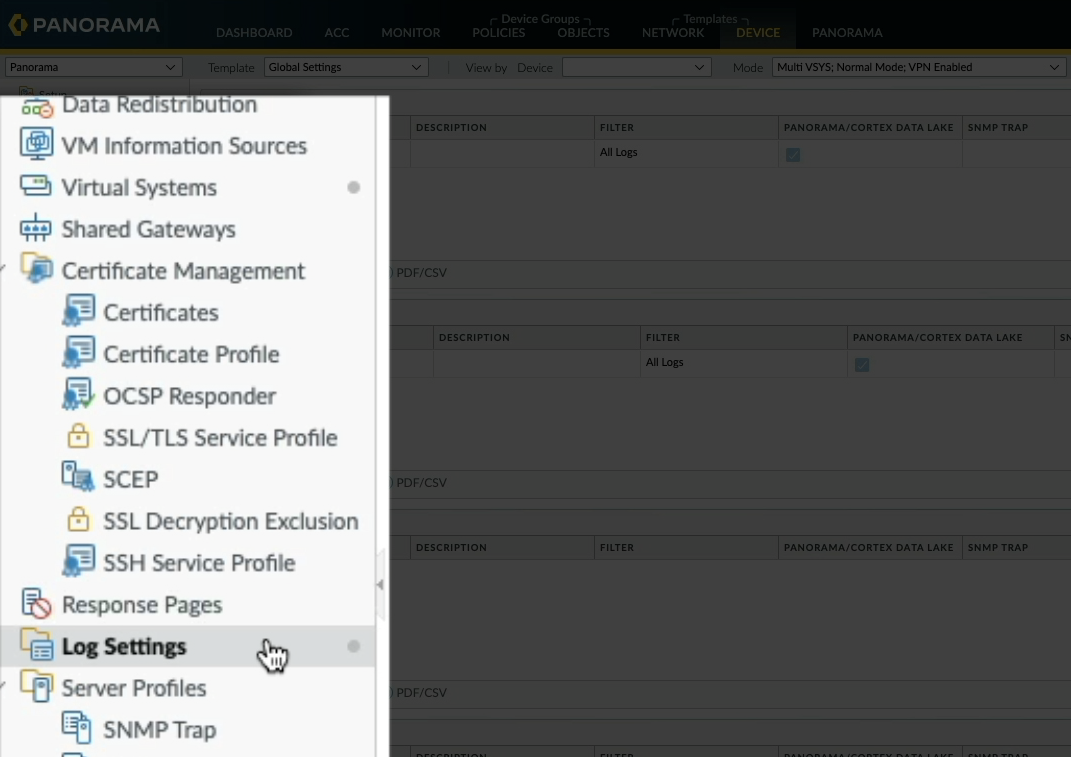
Well if I click on the device tab, which is also part of templates, I can see two small grey dots alongside Virtual systems and log settings, ignoring Virtual systems as this is a default setting and homing on on log settings we see some log configuration. So if you see grey dots next to the configuration sections you know at a glance there is a configuration defined in the template.
What's brilliant about templates is that if I wanted to send all configurations in the Global settings template to any new firewall that is managed by Panorama or maybe even 100 existing firewalls, all I need to do is add the Global Settings template to each template stack.
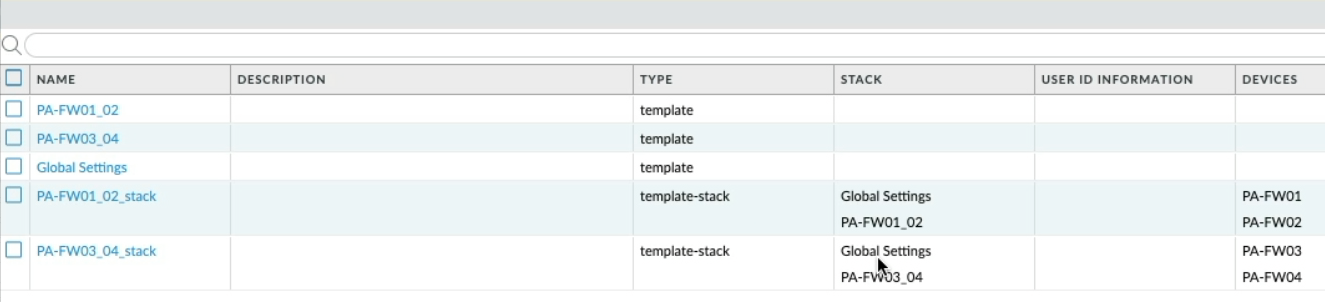
Let me show you, back to the Panorama tab and Templates, in both of these Template stacks, you can see that the Global Settings template is present.
If I open one of these Template stacks, this is where you can add a template to the stack, notice this text down here, "The Template at the top of the stack has the highest priority in the presence of overlapping config"
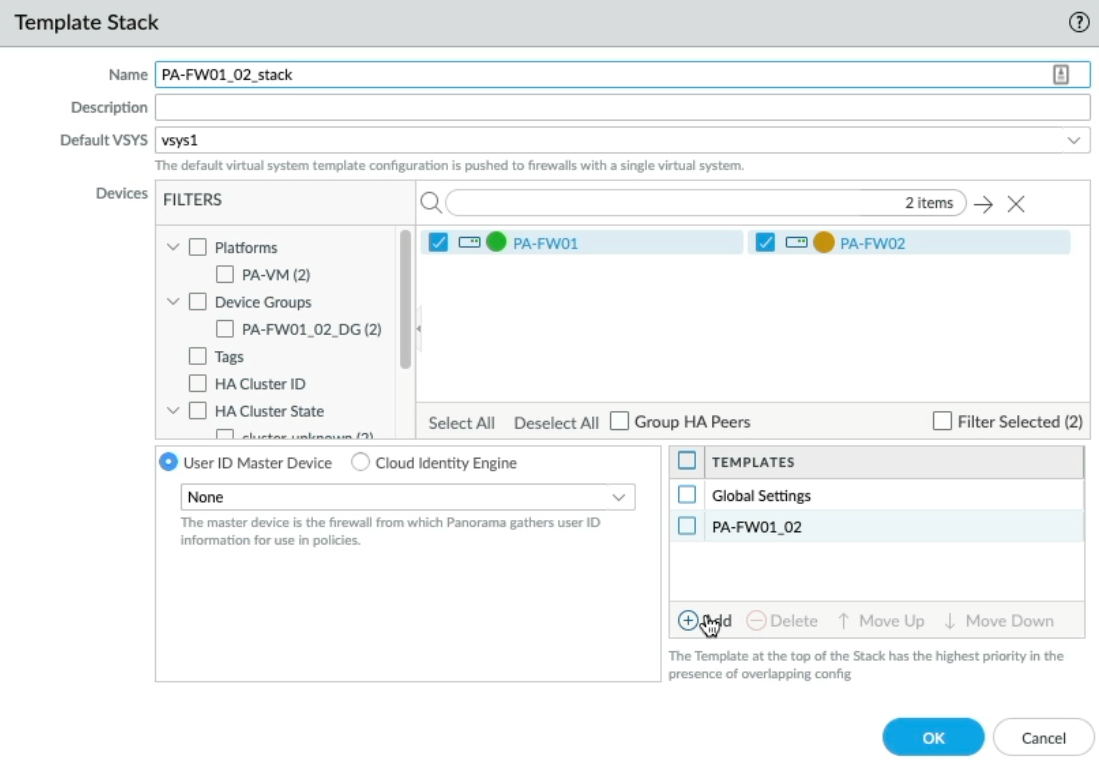
So what that means is if there was configuration in the same fields in multiple templates with the same name, the template at the top would be preferred and that template configuration would be applied.
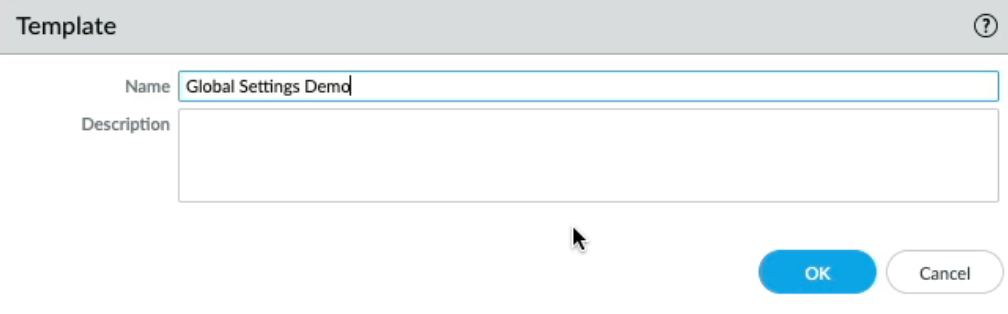
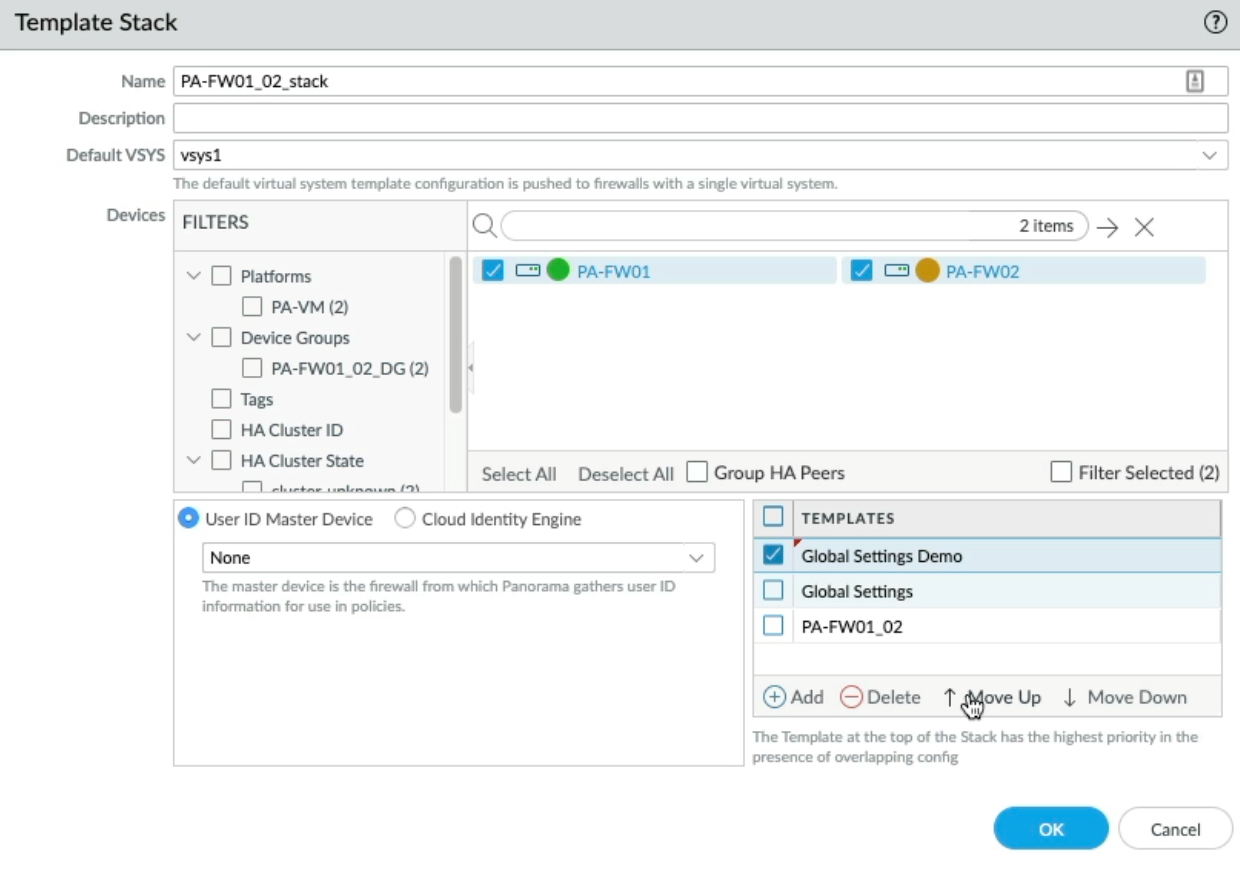
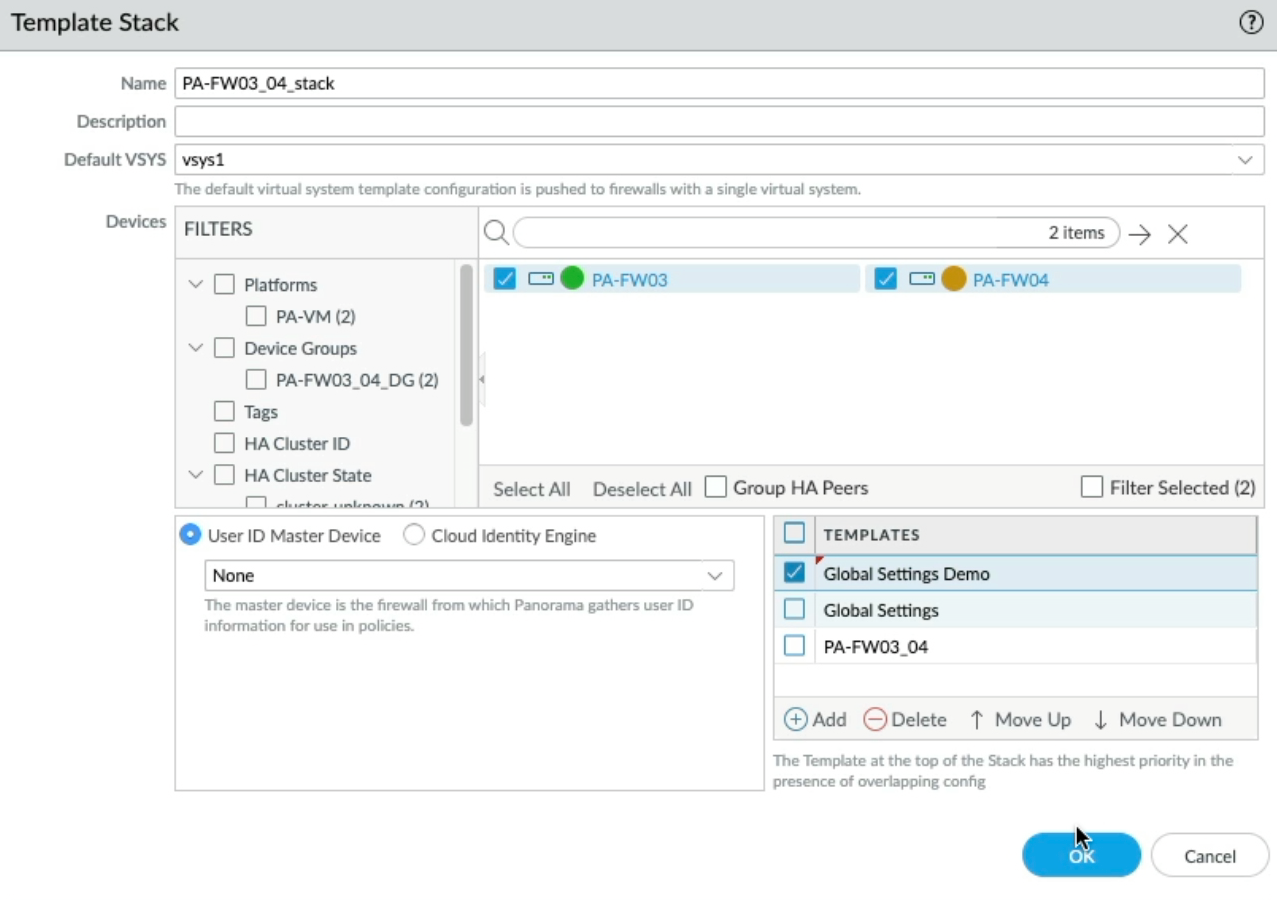
Let me demonstrate this by creating a new template, clicking add, and calling it "Global Settings Demo", Open each template stack and add the new "Global Settings Demo" template and move it to the top.
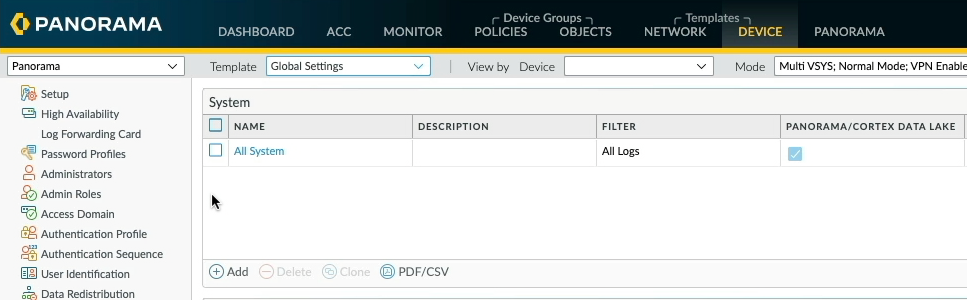
Back to the Panorama Device tab, let's look at the log settings in the existing "Global Settings Template" and take a mental note of the system log settings and add it to the new "Global Settings Demo" template but change the log filter to only log critical severity events.
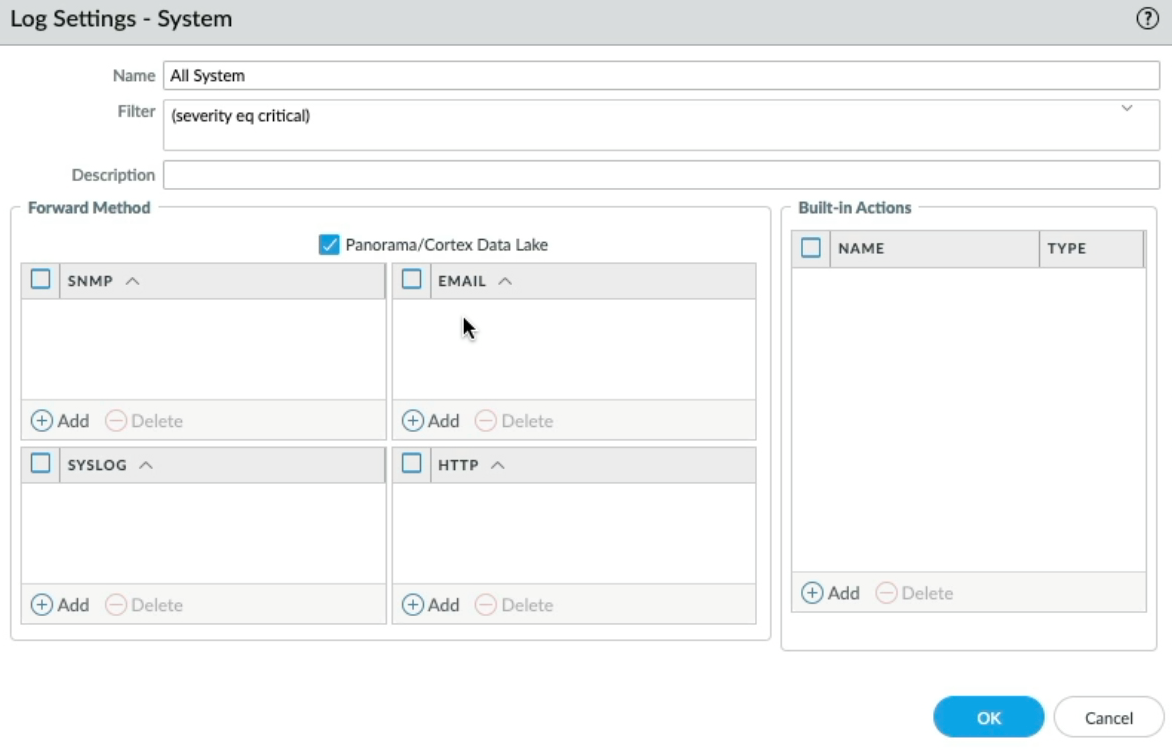
Now, let's open the "Global Settings Demo" template, then log settings and add the name "All System", let's make a subtle change so it's slightly different, let's change the filter to "(severity eq critical)" and tick "Panorama/Cortex Data Lake", and click OK.
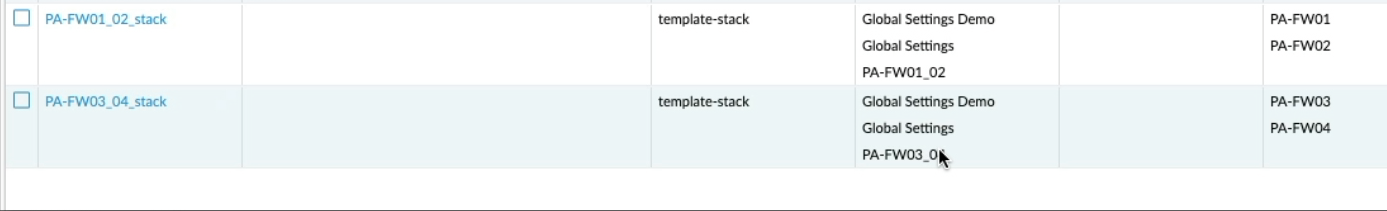
Now back to the Panorama Tab, click on Templates and verify that we have two Template stacks with a new "Global Setting Demo" at the top of the template in each Template Stack. The new "Global Setting Demo" Template should take precedence over the "Global Setting" Template".
We need to commit and push the changes to Panorama and the Firewalls.
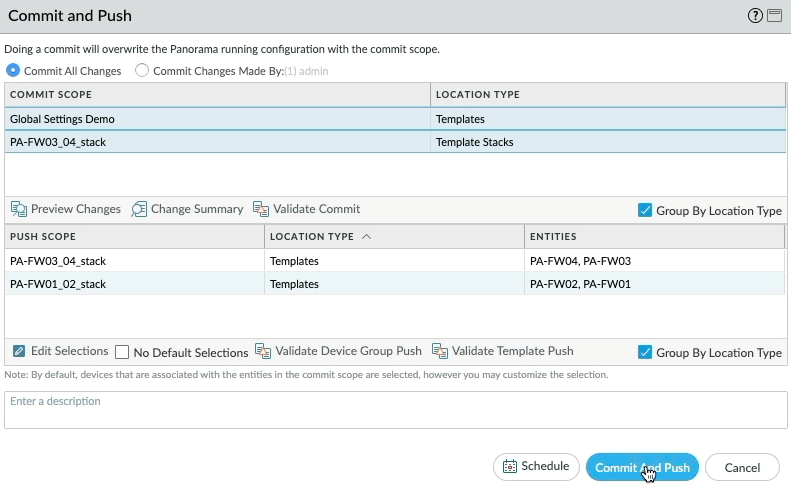
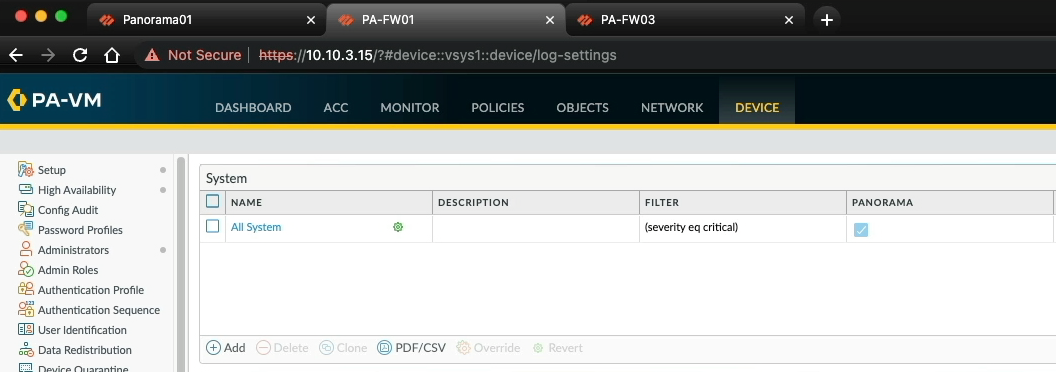
Before changes are made, let's verify the current running configuration on each of the active firewalls, for ease I'm going to browse directly to each of the firewalls so save having to context switch backwards and forwards between Panorama and the managed firewalls. Let's take a look at PA-FW01 first, device tab, Log settings, and we can see "All system" with the filter set to "All logs", and over to PA-FW03 and the same here.
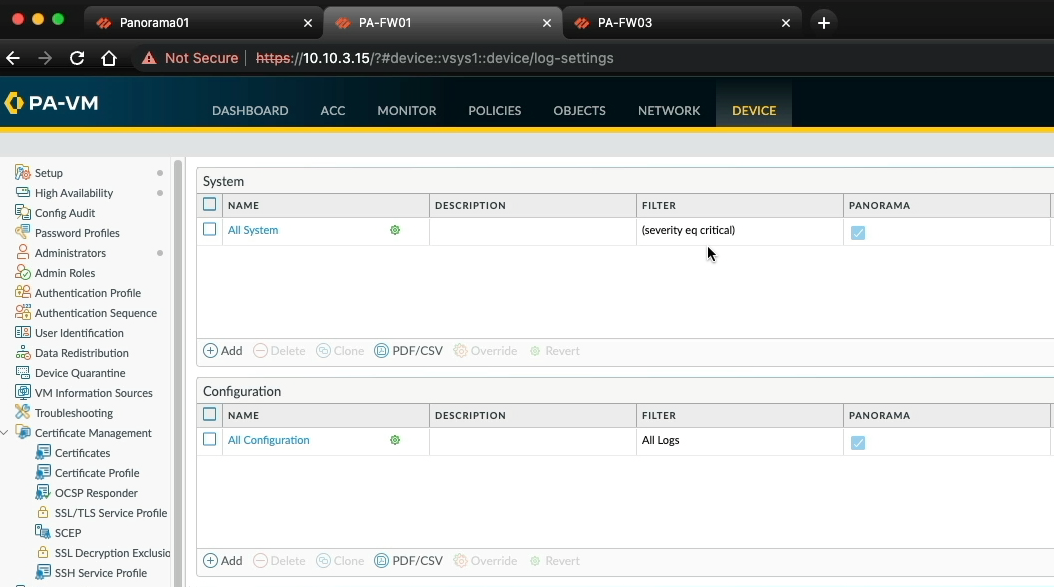
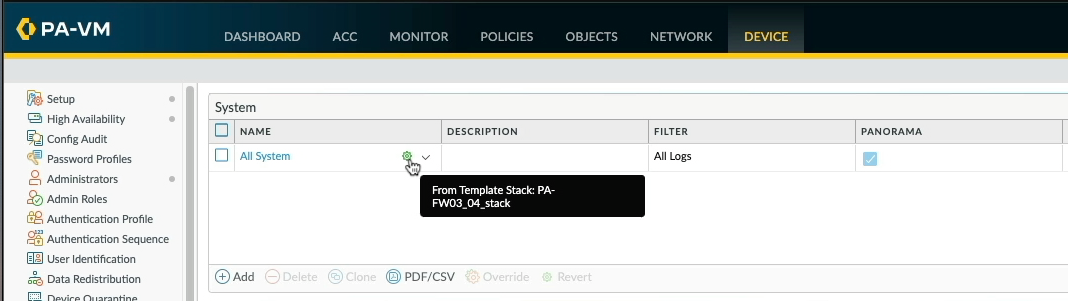
Now that the changes have successfully committed to the firewalls, let's take a look at the outcome. Over to FW01, as you can see the "All System" log settings have changed and replaced by the new "Global Settings Demo" template configuration, while the below Configuration log settings are still intact and defined by the original Global Settings template.
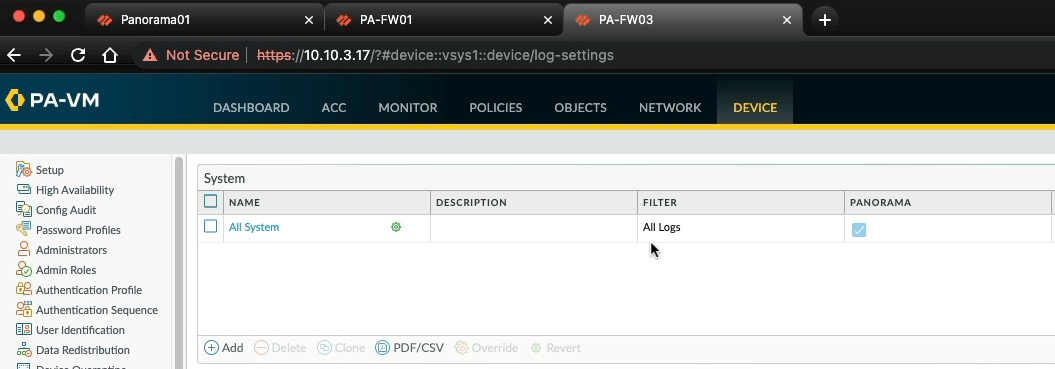
Let's do a quick check of PA-FW03, as expected we have the same configuration here.
If we hover over the green cog, we can see which template stack the configuration originates from.
If you want to watch the original video of this please head over to my Youtube Channel
You can read more about Panorama Templates and Template Stack on the Palo Alto Networks website.